As technology develops as technology advances, so do the risks. Cyber ecosystems are faced with the ever-growing number of threats each day that has brought to threat modeling moving from an intriguing concept in the beginning to become the actual-time standard for information security.
The threat can originate both within the organization and also from outside. To counter the risk of these attacks and prevent unintentional entities from stealing information security and threat analysts use techniques for threat modeling, specifically the STRIDE threat model to ensure that their security measures are in place.
STRIDE Threat modeling is the process of the identification, quantification and management of the security risks that are associated with IT systems. It is a process that IT experts and analysts utilize to find security vulnerabilities and threats that could be posed, assess the severity of these powerful attacks, and implement strategies in place to guard against such attacks.
From an equidistant perspective, every threat modeling techniques promise protection and security against threats. However, in actual scenarios, the methods used to model threats differ from each other in terms of quality, consistency, and value that is realized for the investment. A few of the most popular techniques for modelling threats include the OCTAVE method, Trike threat modelling, PASTA threat modelling as well as the STRIDE method. When we look at the STRIDE method today we will focus on its particulars, its uses and how it differs from the other approaches.
How do I use what is the STRIDE Methodology?
Microsoft’s STRIDE approach aims to make sure that the software meets the security standards of Confidentiality Integrity and Availability (CIA) as well as authentication, authorization and Non-Repudiation. When it comes to cybersecurity, initially, subject matter matter experts create a diagram-based data flow threat diagram. Following that, system engineers and/or other subject matter experts review the application with the STRIDE method.
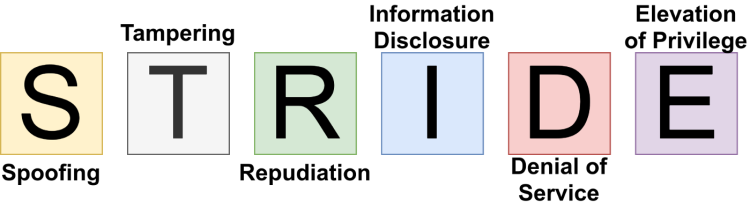
The acronym STRIDE can be described as. It is a reference to
Spoofing
Tampering
Repudiation
Information disclosure
DoS, or Denial of Service (DoS)
Privilege elevation
Spoofing
Spoofing is a different way of saying “impersonating”. In a spoofing attack the attacker pretends to be someone else or system, without revealing and thus evading the authentication. A typical spoofing attack makes use of the less secure authentication marks such as passwords that are simple for a person to figure out (date of birth, surname, username, and so on) or simple passwords with four numbers.
In spoofing processes, the attacker can build dependency through the creation of a fake file. When spoofing a computer attack, attackers employ ARP Spoofing DNS spoofing, DNS spoofing, IP spoofing, or DNS compromise.
Tampering
Tampering happens when an attacker alters something in memory, disks, or on a network. It is a breach of integrity. Only authorized users should have access to information or data that is restricted or intended for only a specific organization or for individuals. If data is not accessible, it’s in order to fulfill a need such as confidentiality or another. Unauthorized access could lead to changes to the data, or even steal it that could have grave implications for the entire organization.
Repudiation
Repudiation refers to negating an idea or plan by claiming that you were not involved in a shady deal that makes it difficult to connect an action to the person who did it. The criminals always prefer to stay secretive, and so they conceal their crimes in a discreet manner in order to avoid being found out.
They might say that they did not do the things they’re accused of. They might claim that they are victims of fraud, or alter or enhance the information that is transmitted through the network in order to create confusion security.
Information Transparency
This implies divulging information that was intended to be kept secret that violates the confidentiality of information. This is among the primary reasons behind breaches of data. Hackers usually do at least one of the following things:
Profiting from bad permissions to database
Access to files that are protected by the veil
File swaps or data retrieval from temp files
Locate the crypto keys in the memory or in a file
Boot or access devices to an OS that is new
Denial of Service (DoS)
Each company has its own system that are able to perform specific tasks. A terminal for instance at the bank. The perpetrators block authorized users from accessing their systems, which is a violation of accessibility. This hinders the business’ activities and causes disruption to workflow and can be employed to blackmail an organization or force the company to pay a fee to facilitate the normalisation of workflow.
DoS is performed against a system, storage or flow of data. The attacker will exhaust the system’s resources through slowing down system performance, or making use of all the existing ‘Enter Password attempts.
Proclamation of Privilege
In granting an unauthorised user inside or outside of a network access to an unrestricted file or virtual location, hackers can carry out an increase in privilege. This is in violation of authorization. Attackers impersonate users by giving them greater access than they actually be granted, allowing them to engage in risks or take harmful actions.
How Spray Foam Insulation Risks Your Property and the Environment
Spray foam insulation has become a popular alternative among homeowners trying to increase their property’s energy efficiency. At first, it...